So your goal is to host a publicly accessible static website from a computer in your home. There are a few problems you need to overcome before even worrying about configuring any software. You need some more basic networking knowledge first.
-
Basic Networking Theory - you should read a brief explanation of the OSI 7-layer network model. You don’t have to try to memorize this and you won’t really understand it until you start actually doing stuff, but you should read it for some basic terminology and to understand that there are distinct steps through which communication between computers happens.
When you start running into problems (“why can’t I access the server? I did all the tutorial steps”), figuring out which layer the problem is in will help guide you to the solution:
- is there a bad cable? -> 1. Physical
- do I have the right IP address? -> 3. Network
- is the firewall port closed? -> 4. Transport
-
Privacy/Security/Safety - don’t host a publicly accessible website from your personal computer. Just don’t. To make this happen you will have to open a hole in your network security that makes your computer accessible from the public internet. Don’t do this on your daily driver computer. Don’t do this with any device that has any files on it that you care about or any access to any personal information. Don’t.
Set up your web server/learning environment on a clean, dedicated system. This could be an old laptop or a Raspberry Pi (an older 3B model will work just fine for this) or whatever cheap computer hardware you have, as long as it can run Linux and has a physical network port (using WiFi will give you extra headaches for getting this working). If you think you might want to expand your projects in the future, you can get a used Dell server for very little money, and add more hard drives as needed. Wipe the hard drive and install Debian or Ubuntu server as a base, there’s lots of resources out there for setting up web services on either.
-
Restricted Ports - you are most likely on a residential internet connection. Most residential ISPs close ports for security reasons, especially 80. For example, here is Cox’s list of restricted ports. You will need to find your ISP’s equivalent list and understand what you can and can’t do with your connection.
There are workarounds, primarily through port forwarding. You will need admin access to your router to set this up. I recommend that you read that entire article because it probably applies directly to your situation.
-
Dynamic IP Address - most people still find it easier to work with IPv4 addresses - I won’t go into IPv6 right now, but you should read a little about it just for awareness. Your residential internet most likely has a dynamic IPv4 address, which means you can’t rely on that address staying the same forever (or even until next week), which means that you can’t configure your Cloudflare domain name to point to a single IPv4 address.
Dynamic DNS is the solution for this, and again you’ll need admin access to your router to set it up.
-
HTTPS/TLS/SSL - if you get through all those issues then you probably have a working website, but now you’re seeing something like this when you try to view it in your browser:
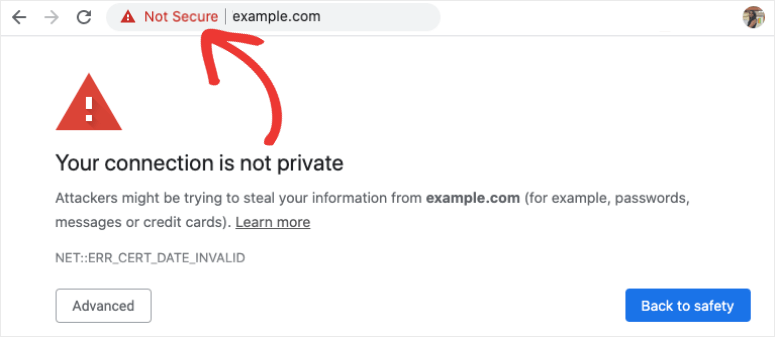
This doesn’t mean that you can’t get to your website - it just means that you can only do it via HTTP and not HTTPS, which the browser is warning you (and anyone else trying to view your website) is not secure. You can either just accept that this alert will always come up, and that you have to click through it, or you can learn about TLS and getting an SSL/TLS certificate. This is a later topic - it doesn’t matter and probably won’t make sense until after you’ve got your web server online.



You’re welcome. I tried to do basically the same thing a few years back (run a WordPress site from a RPi on my home network - and also a Minecraft server) and so I tried to write up the problems I ran into - I probably forgot some, but those are the major hurdles. I learned a lot along the way.
I should also point out that if you rent hosting space (from linode or inmotion or digitalocean or many other options) then problems 1 & 4 become much easier, and 2 & 3 go away entirely (most people don’t host public websites on their home networks because of these and other issues).
Happy to help. If you’re interested in learning networking more thoroughly, I want to point you to Professor Messer especially the Network+ content. He has far more complete explanations than I could write (and it’s free!). Even if you’re not interested in getting any certs, the explanations will be helpful.